It’s always cool to be quoted. This time it was about Microsoft 365 users and how they are being targeted by voicemail-themed phishing attacks.
https://www.darkreading.com/remote-workforce/microsoft-office-365-users-raging-spate-attacks

It’s always cool to be quoted. This time it was about Microsoft 365 users and how they are being targeted by voicemail-themed phishing attacks.
https://www.darkreading.com/remote-workforce/microsoft-office-365-users-raging-spate-attacks

Here is another publication that picked up my quote about Microsoft 365 credential phishing via phishes that appear to be realted to voicemails.
https://www.techrepublic.com/article/targeted-voicemail-phishing-attacks/

It’s always cool to be quoted in an article. This one was about an ongoing vishing campaign using voicemail notifications to steal credentials. An old tactic, but very effective.
https://threatpost.com/voicemail-phishing-scam-steals-microsoft-credentials/180005/

I was tired and ready to relax at home after a fun, but long day out with the family. As we rounded the corner onto our street, I noticed a car parked across the street from my house. This was not completely unusual, but the way that they watched us, edged with excitement, was certainly odd. As we pulled into our driveway, I was surprised to see them get out of the car and start walking toward me, obviously unhappy about something. Before I knew what was happening, I was being confronted about a puppy the people claimed to have bought from me. It seems they had been sitting outside my house for over three hours waiting to pick up the puppy after sending me several hundred dollars through Cash App. The problem is, I never had any puppies to sell, and nobody sent me money through Cash App.
This might have been the first time people came to my house expecting to pick up an item they paid hundreds of dollars for, but it would not be the last. From puppies to PlayStation 5s, this scenario has played out over and over again.
Seems like this is farfetched? Unfortunately, it is not. This scenario happened to a friend of mine, and we have been unable to stop it from happening, over and over again. Not only is it a bad situation for the people being scammed, but dangerous for the person whose house they show up at.

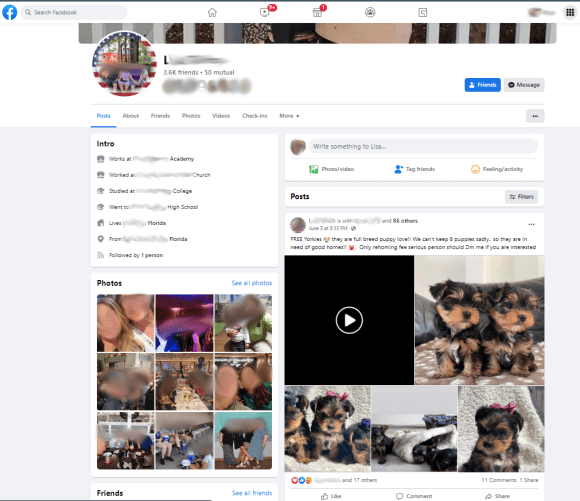
How did this happen? This friend’s Facebook account, let’s call them ‘L’ for short, was stolen by scammers, but not in a way you may expect. You see, it seems these cybercriminals used a stolen copy of L’s drivers license, or a stolen photo of it, to get Facebook to hand over the account to them. Even though L is aware and has reported the account theft and subsequent fraud being committed in her name, Facebook will not take the account down or return her rightful access to it. Even with dozens of others reporting this is a stolen account, Facebook leaves it up to steal thousands of dollars from people, while putting L in real physical jeopardy from people who think she is stealing from them. L has a lot of friends and acquaintances, well over 3,000 friends on her Facebook account, has worked in a local church for a long time and is well known for being a wonderful person. These scammers hit the jackpot when they stole her account. This is not a lookalike account either. They have actually stolen her account, making things much more dangerous.
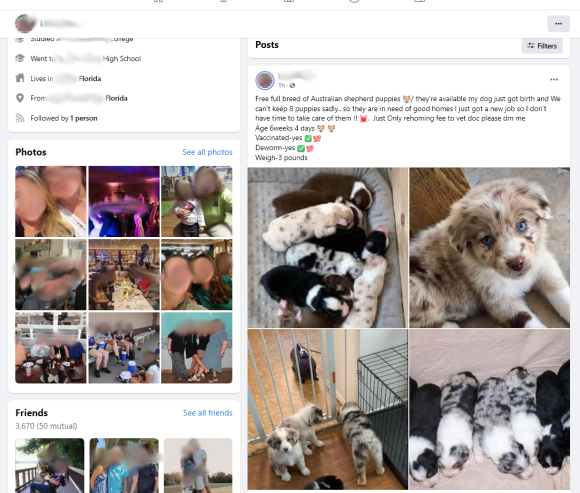
So, how do they get away with this? They are very sly and know how to game the system. I have personally seen posts on her page for the ‘free’ puppies (with a rehoming fee of course, which is where the money comes from) and for PS5s that they bought but cannot keep. They randomly tag a large number of people in these posts, drawing their attention. In all of these past incidents, after scamming as many people as they can, the posts are taken down in a day or so, removing any trace of the previous activity, but pop up a few weeks later to begin the scam again. If anyone attempts to make a comment in the post warning about the scam, the scammers delete the comment and block the person. Because this person is well known, she is tagged in quite a few posts from other people, making it look like her timeline is remaining active. This has been ongoing for nearly six months.
When it comes to ripping off the buyers, they know what they are doing as well. Buyers are rushed into making a decision, worried that the puppies would be claimed by someone else. They are told to pay through Cash App, which is non-refundable or cancelable, and they have even offered the picture of L’s drivers license as proof that it really is her. The scammers will offer to hold a puppy for a deposit via Cash App, asking for the balance in cash later, because they know that stealing some money is better than none, and it helps build trust with the victim. Keep in mind that these deposits are still hundreds of dollars.


Reporting the post has no impact at all, nor does reporting the profile, even after dozens or maybe even hundreds of reports. Facebook has been no help through their automated systems, even though there is an active police report filed with the county Sheriff’s Office. Talking to a person about it is impossible.
The Facebook method of dealing with accounts that have been stolen, is to ask for proof of account ownership by uploading a copy of your identification. This is where the scammers likely supply the image of the drivers license, and Facebook ignores dozens of people who have been scammed or are trying to help stop these criminals. How did they get the image of the drivers license? Odds are it was from one of the many data breaches that occur each week, or it was found after being lost somewhere (although L has not lost the physical copy of her license). Perhaps someone used personal information to get a duplicate, but it is unknown at this point.
Facebook is not the only thing impacted. L has also had to make sure other areas of her identity are locked down, including her credit reports and other areas of her life. Her Instagram account has also been taken over, but worst of all is wondering if the next person there to pick up their puppy after losing hundreds of dollars, is going to become violent.

If you think attacks like this on social media accounts are rare, I have bad news for you. Cybercriminals and scammers know the value of an account, and work hard to take them over. Just recently, a cybercriminal took over one million Facebook accounts in just four months (https://www.techrepublic.com/article/a-cybercriminal-stole-1-million-facebook-account-credentials-over-4-months/), mostly by tricking people into entering their login information in a fake webpage claiming to be from Facebook. Once they took over an account, they would send links to people in that account’s friends list, making the work very easy.
So, how can you protect yourself from being a victim of something like this? It pays to understand the threats to social media accounts.
A major threat is the reuse of passwords across different websites. When a breach occurs that leaks usernames and passwords, cybercriminals often use these credentials in something called a ‘credential stuffing’ attack. This means they try the same username and password in other places such as the major banks, shopping websites, email providers and yes, social media. If the username and password are used there, they will gain access to the account and will immediately change the password to their own. Then, they will change the recovery email address and phone number to ones they control as well, effectively locking you out of your account with no way to reset the new password.
A similar attack called ‘password spraying’ occurs when a cybercriminal takes an email address or username and tries it along with the most commonly used passwords, such as ‘12345678’ or ‘qwerty’, etc. There are lists of the most common passwords posted every year and they do not change very much. Just like in the above example, they then change passwords and contact information and essentially own the account.
In these two cases, having strong, unique passwords can make all the difference between keeping your account or losing it. To help manage these unique passwords, look into password managers, which are usually free or low-cost tools that help generate and protect passwords for you.
Multi-Factor Authentication (MFA) is another great way to help secure accounts. While it adds another step to the login process, it really helps stop cybercriminals who somehow guess or steal a password to an account. MFA is widely used in banking and is where you get a code via a text message, or type in a code that is generated in an application on your smartphone. This way, to log in, an account thief would need both your username, password and the code, making it much tougher.
Finally, any time a link takes you to a webpage that is asking for login information, be very careful. Make sure the URL of the login page is really from the website (facebook-login.com or login-facebook.com are NOT Facebook websites for example) and ask yourself if there really is a reason you would need to be logging into the account again.
Please understand the dangers of social media accounts and the potential nightmare they can become and protect your account just like you would your bank account. Not only can things get ugly online, but they can also become a physical threat, such as in the case with L.
Edit: They are back at it on July 01, 2022, just in time for the 4th of July holiday
Edit: there was another posting up as recent as July 11th, 2022, but it has been removed as of July 13th, 2022

I had a chance to sit down at BH 2021 and chat with Scott Schober, whom I have known for quite a few years now. I always enjoy our conversations and find they get me thinking about things in a new light. Enjoy!


I have been hearing some interesting things from the RSA conference this year. That is nothing new, as RSA is a great source for the latest in cybersecurity technology and a wonderful place for education. Unfortunately, I was not able to attend RSA this year; however, one trend that I have heard about involves something near and dear to my heart, and it concerns me.
On more than one occasion now, I have been told that this year, well respected speakers have said, on stage, that Multi-Factor Authentication (MFA) can stop 99% of phishing attacks. This is not only a foolish statement, but a dangerous one. It is also not the first time I have heard this claim or the first time I have addressed it.
Looking back to 2018 when I first read the headline, “Google: Security Keys Neutralized Employee Phishing” from Brian Krebs, I have had serious issues with how MFA is explained. That article started with this quote, further misleading people:
“Google has not had any of its 85,000+ employees successfully phished on their work-related accounts since early 2017, when it began requiring all employees to use physical Security Keys in place of passwords and one-time codes, the company told KrebsOnSecurity.”
Not only are statements like this misleading, but they are also just plain wrong and even dangerous.
Ironically, shortly after this article was published quoting Google telling us about how MFA keys did such a great job eliminating phishing, the marketing giant launched the sale of these same MFA keys. This was not an accident, but rather a clever marketing scheme.
I do not want to give the wrong impression here. I actually really like MFA and recommend it to people all the time. I support the FIDO Alliance wholeheartedly and use Yubikeys myself. The issue is that it is not the silver bullet that some people claim it to be. While it can be effective at stopping some phishing attacks and other very specific types of attacks, it is mostly useless against the vast majority of them. MFA protects account logins – that is all.
Why would I make such a bold statement? It is simple really. While MFA helps to prevent accounts from takeover due to lost, stolen or weak credentials, it does nothing to counter a person clicking on a link to a malware-infected website, opening an infected document or wiring money to bad actors. According to the FBI , between June 2016 and December 2021, there were over $43 billion in losses due to Business Email Compromise (BEC). While the name implies that accounts were compromised, the majority of times these scams are pulled off by simply spoofing the name of an email account, not actually having access to the real account. MFA does nothing to stop a spoofed account from asking someone to transfer funds or buy gift cards.
Another huge part of email phishing is the distribution of malware. This most commonly happens by getting the targets of the emails to click on a link in the email or by opening an infected document and enabling active content or macros. None of these scenarios are impacted by MFA in the least.
By telling people that MFA will stop 99% of phishing attacks, we are doing a great disservice to people by giving them a false sense of hope. Executives could come back from the conference and tell their staff that if they implement MFA, they can cut in other places, which is a really dangerous message.
Phishing cannot be stopped by a single technology or even a mix of technologies. The best we can do is to manage the problem and reduce the risk through a mixture of technologies and by helping individuals spot these attacks through education and practice. A focus on a good, strong security culture within the organization can do far more than simply enabling MFA; although these measures are an important part of a strong security program.
As security professionals, it is our duty to be objective about how effective security controls are and not fall for marketing messages that are meant to promote products. Snake oil is still too prevalent in our industry to let our guard down.


Inevitably, there is bad in the world — some of it evil, perpetuated by evil people, some of it just bad, caused by natural or man-made events, but without malice. In the wake of another evil act here in the U.S., we are also starting hurricane season, the time when we face the strong likelihood of natural disasters as well. Yet another situation we face following any tragedy is that of scammers taking advantage of the generosity and caring of people.
It never seems to fail. In the wake of a hurricane, tornado or even man-made event, pleas for help go out and people respond. While this represents the best in people and is absolutely wonderful, many of these awesome deeds and donations can easily end up in the hands of scammers. For this reason, it is important that we help the people who need it, not the unscrupulous people who prey on good people. As humans, when we are in a state of high emotions, we can easily overlook signs of misrepresentation that we would otherwise spot easily. This is why they go on the attack after a major, heart-wrenching attack.
If motivated to help the victims of these events, we should be cautious indeed. If the request for help comes from an unsolicited email or a social media post, care should be taken to ensure the organization is legit. A quick web search will often turn up information about the charity and help guide you past the scams. See if there are recent Form 990 tax records filed (for U.S.-based charities) and look for financial reports that can show how much actually goes to the victims. If the charity is well-known to you already, it still pays to be careful by browsing straight to the charity’s website rather than clicking on a link in a post or email. If the charity is raising money to help, you can bet there will be a mention of it on their website along with instructions on how to donate securely.
While tragedy will occur in this world, we can ensure that the intrinsic good from people can prosper by taking a few moments to make sure our help goes to those who need it, not scammers or cybercriminals.

Cybersecurity is often thought of as a technical field, one in which some geeks gather up cool tools and fight the battles on the front lines, defending our organizations and personal use from the constant onslaught of cyber attacks and scams. While there may be some truth to that, we do love high-tech tools to help us defend our networks, there is a whole part of cybersecurity that has little to do with blinky boxes and the destruction of electrons, and it might just be the most important part – the people.
Yes, most of us know that people are the targets of cybercriminals looking to get into networks. Phishing emails, phone scams and attacks via text messages are all things we are aware of and even the most tech-focused cyber geek understands that they are the number one way networks get compromised. Educating users about this is incredibly helpful, but there is more to it than just that. Maybe you are an introvert and do not really like dealing with users very much. Maybe you would rather be in a server room full of noisy fans and too-cold AC on one aisle, and too-hot air on the next. I really do not blame you; however, what we are about to discuss can make dealing with users a bit easier, and possibly reduce the number of times you have to do it at all, significantly.
Grab some coffee or some tea and get comfortable (not too comfortable though) and we are going to talk about what may be the least exciting, but most important thing in cybersecurity – policies.
If I did not lose you there with a loud groan and dash for the nearest door, great. I know it is not the most fun topic, so I will excuse the momentary fight-or-flight response, but stick with me for a few moments and you will see how thinking through policies can make your life only slightly less enjoyable than a week in Maui. Okay, maybe that is a stretch, but it might make the trip to Maui possible through a lower workload, meaning more vacation days, some of which could involve Maui.
A Real Problem With Policies
One real problem I see with policies is that they are poorly thought out, and bad policies can and will lead to people finding ways to get around them, resenting them, and possibly resenting you and your team as a result. That is the real story here…thanks for coming to my TED talk.
What Do We Do About It?
If you are still reading after my above revelation, it means you probably want to know how to make better policies that do not result in coworkers tainting the coffee creamer you keep in the break room fridge, with salt. Please do not ask why I used that example. I have had better days.
Here is the trick to writing policies that do not stink. Think about the repercussions from the end user’s perspective. We often write policies that make no sense to them, even if it is the right thing to do. We simply cannot expect users to follow policy, something that may make their job a bit tougher, without them understanding, at some level, why. We also need to recognize when policies no longer make sense and be willing to revise them, so they do. “But we have always done it that way” is no excuse for draconian rules and medieval penalties.
A Recent Example
I have had a couple of jobs in my career that required significant travel. One was even before 9/11. I will NOT use the resulting security changes from that as an example. I just will not. I like to get through the checkpoints quickly and will not risk angering people from ‘that’ organization. I will, however, use our recent and ongoing pandemic and its associated rules with reckless abandon.
Having spent a lot of time in airports during the pandemic, I have come to loathe some of the rules that are currently in place, especially with respect to masks, and I am not alone. This is not a pro or con, as it relates to mask effectiveness, but is about the current rules and how people are acting with respect to them. We can learn a lot about policy from watching how things play out, especially when the policy has such significant enforcement measures behind it, something we are not likely to have ourselves.
The current federal mask policy for air travel says this:
“Persons must wear masks over the mouth and nose when traveling on conveyances into and within the United States. Persons must also wear masks at transportation hubs as defined in this Order”
Here are all 11 pages of the order if you would like to read it. This was published on January 29, 2021, extended through September 13, 2021, then again until January 18, 2022, followed by March 18, 2022 then April 18, 2022, and now for another two weeks.
Now this order, or policy, has the backing of the federal government, which has applied pressure on the airlines and airports to enforce the policy. In the beginning, enforcement was rigid, however, as time has gone by, the enforcement has become a bit more lax, well, at least in the airports it has. On the aircraft itself, it seems to be hit or miss. It is not uncommon at all to see people walking through the airport with no mask at all, a mask hanging off one ear, or only covering their mouth and not their nose, and unlike in the early days, nobody really says anything. So, why is this happening? We can learn a lot from this example.
First, people may go out to see a movie in a crowded theater, then have a meal in a crowded restaurant, and grab a drink in a packed bar, all without a mask, then when they get to airport, one of the last bastions of public mask wearing, they are told they must wear one. For many people, this simply does not make sense. As the world around them has relaxed, this policy may feel prehistoric, so they look for ways around it.
At some point, people look for, and discover, loopholes in the policy. For example, some enterprising person realized that in the airport terminal, if you hold a drink or food in your hand, you can get around the rule using the “I am eating/drinking” defense to sit around with no mask. I even heard a person on a phone call bragging about how they were bucking the system like this, although I have not seen anyone enforce a mask policy at the gates or in the airport in a long time. On the aircraft, this may or may not be enforced as well, which brings me to another problem.

If your policy is not enforceable or is enforced inconsistently, people will ignore it. This is where things can get a little tricky and careful planning can pay off in a big way. Let’s say you have a policy that forbids online shopping from company-owned devices, and perhaps you even have a proxy server or some other tech enforcing it, but then the organization also requires people to get three quotes on an item prior to making a purchase, or to look into the best options for the money. You make that nearly impossible as people cannot price check or even read product reviews from shopping sites. This means you must start making exceptions, a very slippery slope indeed. If you allow Alice in Finance an exception, Bob in Marketing may argue that he should get an exception too, etc. and so forth until almost everyone has an exception to the policy, making the policy pointless, tedious and ultimately frustrating for you and the other employees.
Why Well Thought Out Policies Matter
In a case like this, how much of a security risk would it be to allow access to online shopping services from the start? This would eliminate animosity (along with the probable salting of one’s precious hazelnut coffee creamer), impact morale in a positive way while not really impacting security in a negative way, and it would reduce the temptation to perhaps find a web proxy service that would still take you to a shopping website, while appearing not to. I have heard that may or may not have been a ‘thing’ at a past employer, especially back when Woot-Off!’s were a serious manner. (I’m not the only one that rembers Woot! when it was great, right? Comment below!) Totally hearsay though. Totally.
There will be times when policies really do need to be firm with an allowance for some, but not many, exceptions. It is a fact of life, however, when you write the policy, try to anticipate where these exceptions may be required and account for it in the policy. Also, have a well-defined process for requesting and managing these exceptions, either permanently or temporarily. The less frivolous policies you have in place, or ones that the users do not understand, and the more consistently these policies are followed, the more likely they are to follow the policies that really matter. The less that policies need exceptions, the less interaction you must have with the (oftentimes frustrated) users. That is a huge win right there.
In addition, reviewing the policies on a regular basis is very important. I do not mean opening the document, changing a date and calling it ‘reviewed’ for compliance reasons, I mean really considering if it is still valid and important. You may have installed some technical controls that mitigate the risk you were trying to address in the policy or perhaps the way people are working has changed. If a policy is no longer needed, can it be removed or changed? It is one less point of friction and one less thing to maintain.
Summary
Remember that as cybersecurity professionals, our job is business enablement, not being the “Department of No”. Eliminating friction between ourselves, the users, and other business units has always served me well. Having reasonable policies and considering where policies may cause friction can be the difference between someone bypassing a policy when it does cause a security risk and following it. This also helps contribute to an improved overall security culture, as the users can understand that policies that are in effect are there for a reason, especially if you educate them on the reason behind the policy.
Don’t forget to subscribe to the blog for future updates!


Every February, the city of Las Vegas plays host to many of the biggest names in consumer electronics at the annual CES conference. For many organizations, this is the show where they release their new cutting-edge products or show their vision for the future. From the latest in smart toasters to AI-powered concept electric vehicles, this show covers it all. In 2020, over 4,500 organizations participated in the show, which encompassed over 2.9 million square feet in venues all around the Las Vegas strip.

This is heaven for a geek like me, and I was finally able to attend the show this year. My goal, besides just geeking out at the new technology, was simple. I wanted to chat with vendors about the security of their products, especially those that are being targeted for home use. In the age of internet-connected refrigerators and cheap cloud-connected home security cameras, we are connecting Internet of Things (IoT) devices to the internet at an amazing pace. It is estimated that there are over 46 billion connected devices out there, an average of 10 devices per household. With all of these connected devices being installed in our homes, I had hoped that security would be a significant focus, however, even now, this does not appear to be the case.
Why Security Is a Concern in These Devices
You might ask yourself why security would be a concern with these devices. I mean who really cares if a refrigerator has a security vulnerability, what is the worst that can happen if a fridge gets attacked? Well, unfortunately a lot of things can happen, and few of them good. Here are a couple of scenarios.
Imagine going to the refrigerator to get a cold glass of milk, and on the screen is a message saying if you do not pay some cybercriminals several hundred dollars soon, your fridge would stop working. This is called ransomware and while not a serious threat to your typical household appliances right now, it is just a matter of time. Ransomware has become one of the biggest threats to networks in organizations in modern times, and there is very little keeping them from targeting homes as well. With the cost of refrigerators rising to several thousand dollars, who would not pay a few hundred to keep it from becoming trash? If you are relying on a warranty to fix this, you are likely out of luck, just as if someone broke into your home and wrecked it.

Another scenario is a cybercriminal using your device and network to attack other organizations. A Distributed Denial of Service (DDoS) attack is where a bad actor sends a lot of internet traffic to a target, crashing their website or even making their network so slow that they are unable to function. Cybercriminals can use these attacks to extort money from victims, or they may just pay for a service to cripple the target. These attacks are often made possible through the use of botnets, or large groups of infected devices with internet access that the bad actors control and the frequency of the attacks is up. There was a 173% increase in these attacks just between Q3 and Q4 of 2021
(https://portswigger.net/daily-swig/report-ddos-attacks-increasing-year-on-year-as-cybercriminals-demand-extortionate-payouts). Yes, your trusty fridge might have a dark side, attacking hapless victims while also keeping your vegetables fresh, and you may never know it.
These devices can also be used as a way to get inside your network and to help cybercriminals steal information from you, or to spread viruses within your home network as well. Not only are refrigerators a possible target, but any internet connected devices can be used for these purposes and more. Imagine cybercriminals being able to access video or audio feeds from security cameras, or any device in your home that has a camera or microphone built in. This has happened and will continue to happen again.
Alarmingly, many small businesses also use these consumer-grade devices within their organizations, never considering the risks they are taking. From a cost standpoint, this makes sense as enterprise-level cameras and devices can cost twice as much or more, and offer features that small businesses really do not need.
What I Discovered at CES
I was hopeful that somewhere in the 2.9 million square feet of electronics showroom, I would find at least some manufacturers who really touted the strong cybersecurity of their product as a key feature. I was sorely disappointed. What I did find was a lot of blank looks and referrals to other people who were also unable to answer any meaningful questions about the security of their products.
Some of the key questions I asked these vendors were related to how long they expected to support security updates on the devices they are selling, how they handle someone reporting a security issue to them and how security patches were installed.
OK, I get it, these are often salespeople or marketing people, not security gurus. I did not expect them all to have answers to my questions right away. However, I was hopeful that someone at the show could answer some basic questions. In most cases, I was mistaken. Not one vendor I spoke to could tell me how long they would commit to providing security patches for the products that were for sale. While this may not be as critical in a cheap webcam (it is still an issue), where it was very critical, such as connected electric vehicles and cars being manufactured by companies both small and large, there was also no commitment.

It is important to understand that automobile manufacturers are increasingly leaning on technologies such as self-driving features, which make use of computer controlled accelerating, braking and steering, among other things. One major automotive group has called themselves a, “sustainable tech mobility company”, not just a car manufacturer. When I asked about future updates for these vehicles, I was told that they would be supported for, “Quite some time”. Imagine that 12 years from now, it is discovered that a bad actor could access your vehicle via the wireless hotspot or smart phone app, and take over your steering, gas pedal and braking, all while you are driving down the road. Now imagine if the auto manufacturer has stopped supporting security updates to that vehicle. While this sounds like a scary thing worthy of the tinfoilest of hats, if we do not ask the questions now and get some commitment from the manufacturers, we could find this as a real issue. As recently as 2015, Chrysler recalled 1.4 million vehicles after a couple of car hackers were able to disable a vehicle while it travelled down the road at 70 miles per hour. Sometimes the tinfoil is not overkill.
Even if vehicles are not being taken over while driving down the road, other issues still arise. I happen to have a car that is high on the list of those stolen. As a matter of fact, my Dodge Challenger is almost three and a half times more likely to be stolen than the national average here in America. This is in part because they have been shown to be very easy to steal by simply programming a new key to the car. You do not even need to have another key present to do this. In less than a minute, through a flaw in the infotainment system, thieves can add their own key and drive off. Dodge has issued a security recall for this issue where they no longer allow additional keys to be added to the car once locked down, however, while friends with 2019 and 2020 cars have received notifications about the update, I have not received notice for my 2016 model. Until I do, I will not drive my car to the airport, a prime spot for thieves of these cars.
This issue is not just limited to the organization that makes my car. The more computers we put in cars, regardless of the manufacturer, the more likely issues like this will arise. This is why we need a commitment for future security fixes.
Moving away from vehicles, I also spoke to several smart home device manufacturers, including those who made smart door locks, and none of them were able to confirm a commitment for future support.

My Conclusions
All of the walking, all of the questions, and all of the research I did at CES illuminated a couple of things. First was that security is not a key part of these manufacturing organizations’ culture. If security were a key part of the organizational culture, I would have received far less blank stares when I asked even the most basic security questions, even from salespeople. This is a trickle-down effect where a strong and good security culture at the top levels of management eventually influences those throughout the organization.
The second thing is that people are not asking about security when making purchases. If they were, the staff at the booths would have been more prepared to answer them. This is a trickle-up effect. If people do not care to ask for improved security, the salespeople and marketing teams are not going to waste time learning about questions they do not have to answer. As unfortunate as this is, I cannot blame them for this.
As consumers, it is time that we start asking questions about the security of our devices, especially when we are connecting them to our home networks. These are the same home networks where we do our banking, tax filing and other potentially sensitive things. Along with asking about security, it is time that we show these manufacturers that it is an important issue, by buying items that do promote security over those that do not. Many of these smart home devices are sold based on the lowest possible price point being the winner, however, as consumers, it would be very beneficial for us to spend an extra dollar or two for devices that are serious about security. Once this becomes a differentiator with buyers, manufacturers will find it much easier to invest time in security research, and may be far more likely to commit to support of the devices for several years down the road.
Do you have thoughts on the future of security in consumer devices? Let’s hear them in the comments.